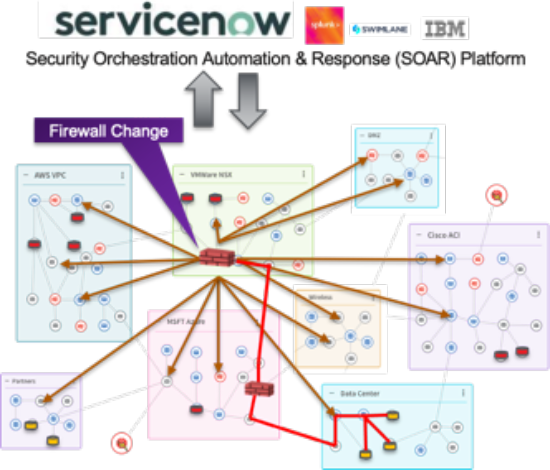
Understand the impact of changes to security rules
RedSeal Network can save thousands of man-hours by integrating via APIs with your change management workflow. Before a change is implemented, review policies and requirements automatically. After a change is implemented, verify that all changes are properly documented and report on incorrect implementations.
RedSeal Network provides the ability to run a security impact (“What if”) analysis to test the strength of your security posture across multiple factors. Security teams can model and verify changes to their on-premises and/or cloud environment prior to being implemented. The overall result is an acceleration in change request and organizational savings.
Security impact analysis calculates potential traffic flows between specified end points and/or subnets and shows what vulnerabilities on the destination would be exposed to the system defined as the source if the specified access were enabled and open. Information such as exposed vulnerabilities, hosts reachable, downstream access and potential threats are highlighted if the ‘what if’ conditions were enacted.
Security teams can obtain valuable insight into the status of existing and proposed paths between critical hosts and endpoints, discovering if certain ports and protocols are open and in use. System exposure is highlighted to pinpoint potentially untrusted and trusted subnets as well as network devices that are considered protected, directly attackable, or indirectly attackable. Furthermore, how many vulnerabilities – and their CVSS impact – are (or would be) exposed by permitting access through the specified port and protocol are reported, including ‘leapfroggable’ downstream vulnerabilities.
With comprehensive security impact analysis and integration with your change management workflow systems, discover:
- Details of paths between hosts, endpoints and/or subnets
- Potential attack vectors
- Impact of threat vectors
- Downstream risk associated with configuration changes
- Compliance impact with policy rule changes