Being Digitally Resilient in the Face of HIDDEN COBRA
Watch Video: RedSeal and Hidden Cobra Overview, Use Cases and Demo
Introduction
On November 17th, the United States Computer Emergency Ready Team (US-CERT), in conjunction with the FBI, released a pair of advisories about the North Korean hacking and espionage campaign code named HIDDEN COBRA. The latest advisories describe two pieces of malware called Volgmer and FALLCHILL, which have been actively used to attack enterprises and other commercial entities in the US. Since 2013, organizations in the aerospace, telecommunications, and finance industries have been targeted with spear phishing campaigns.
The US-CERT advisories provide both a detailed analysis of how the underlying malware packages function as well as the detection signatures and the observed IP addresses of the command and control (C2) infrastructure. This data can be used to detect the malware on your network and sever access to its controllers (Volgmer C2 IP Addresses: CSV STIX; FALL CHILL C2 IP addresses: CSV STIX). US-CERT’s previous HIDDEN COBRA advisories from June also reveal several vulnerabilities (CVEs) that North Korean threat actors are known to target and exploit.
This article will describe how the Volgmer and FALLCHILL malware operate, what they target, how they infect those targets, the potential impacts of these infections, and effective mitigation and remediation strategies to protect your enterprise.
Summary of Suggested Actions:
- Identify and eliminate outbound network traffic to the C2 infrastructure.
- Perform a risk-based prioritization of vulnerabilities to patch on accessible and high-risk endpoints
- Run RedSeal’s incident response query to efficiently isolate and contain any observed indicators of compromise.
About the Volgmer and FALLCHILL Malware
Both malware packages are Windows binaries consisting of executable files and DLL counterparts able to be run as a Windows service. The primary method of attack has been through targeted spear phishing campaigns that trick victims into opening malicious attachments or clicking links leading to malicious websites exploiting browser-based vulnerabilities.
Volgmer
The Volgmer package contains four distinct modules, a “dropper”, two remote administration tools (RATs), and a botnet controller.
- The Volgmer dropper, a Windows executable, creates a Windows registry key containing the IP address of external C2 servers. It then installs its payload (either a RAT or the botnet controller), achieving stealthy persistence by overwriting an existing Windows service DLL with the payload. Finally, it can clean up after itself and remove all traces.
- The RAT payload, after achieving persistence on the infected Windows machine, communicates back to its C2 infrastructure over ports 8080 or 8088. The RAT enables the attacker to take over the infected computer, executing arbitrary code and exfiltrating data.
- The botnet controller can direct the activity of other compromised computers to orchestrate DDoS attacks.
FALLCHILL
The FALLCHILL malware is a remote administration tool demonstrating a heightened degree of sophistication in its ability to remain hidden, as well as an advanced communication mechanism with its C2 infrastructure. FALLCHILL masquerades as a legitimate Windows service randomizing across seemingly innocuous service names. It generates fake TLS traffic over port 443, hiding the C2 commands and communications in the TLS packet headers, which then get routed through a network of proxy servers.
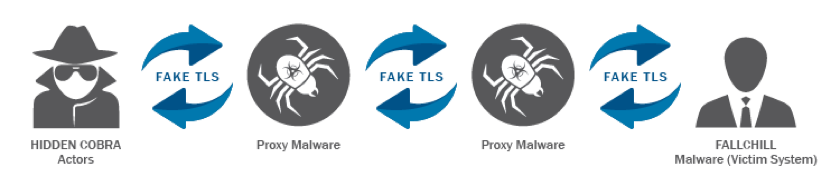
How the Malware Spreads and Impact of Infection
Although both malware packages are primarily distributed via targeted spear phishing campaigns, they have also been observed on malicious websites. This increases the chances for opportunistic drive-by-download infections. These targeted attacks have been seen in the US aerospace, telecommunications, and financial services.
A successful infection will result in the HIDDEN COBRA threat actors having persistent access to and control over compromised computers. The remote administration tools allow them to modify the local file system, upload files, execute files or any arbitrary code, as well as download anything on the file system. The result is that attackers will have a hidden backdoor to your system and can execute any arbitrary code. Thus, in addition to being able to exfiltrate local files such as documents directories or Outlook databases, the infection establishes a beachhead into the rest of the network from which future breaches can be staged.
General Mitigation Advice
Enterprise security organizations can take several steps to mitigate the risk of a successful spear phishing or drive-by-download infection. In the past few years, attackers have, with increasing frequency targeted end user workstations to exfiltrate local data and establish a beachhead into the rest of the corporate network. As a result, it is increasingly important to expand vulnerability management programs to include regular scans of workstations and laptops followed by timely patching of any discovered vulnerabilities. Employees, particularly executives and those exposed to sensitive or proprietary data, should be trained on practicing good email hygiene and being vigilant for possible phishing attacks. User workstations should be configured according to the principle of least privilege, avoiding local administrator level access where possible. Additionally, the US-CERT also advises limiting the applications allowed to execute on a host to an approved whitelist, to prevent malware masquerading as legitimate software.
RedSeal Can Increase Resilience and Decrease Risk
RedSeal users can decrease their risk of exposure by identifying, closing, and monitoring access from their networks to the HIDDEN COBRA C2 infrastructure. Moreover, in the event of a detected IOC, RedSeal allows you to accelerate incident investigation and containment to mitigate the impact of an infection.
1. Identify and close any existing outbound access to the C2 infrastructure
The first step is to make sure you eliminate or minimize outbound access from your networks to the HIDDEN COBRA C2 infrastructure. Since the C2 IP addresses point at proxies across the world that relay commands and data to and from the threat actors, many are associated with legitimate entities whose servers have been exploited, or commercial hosting providers whose servers have been rented. To locate access from the inside of your network to any given C2 address from the advisory, use RedSeal’s security intelligence center to perform an access query from an internal region to the internet, and in the IPs filter box, enter the IP address from the US-CERT data.
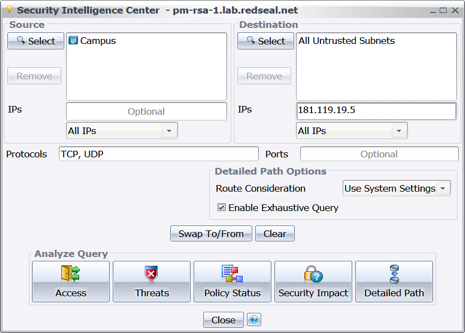
Figure 2: Running an Access Query from the Security Intelligence Center from internal to C2 Infrastructure
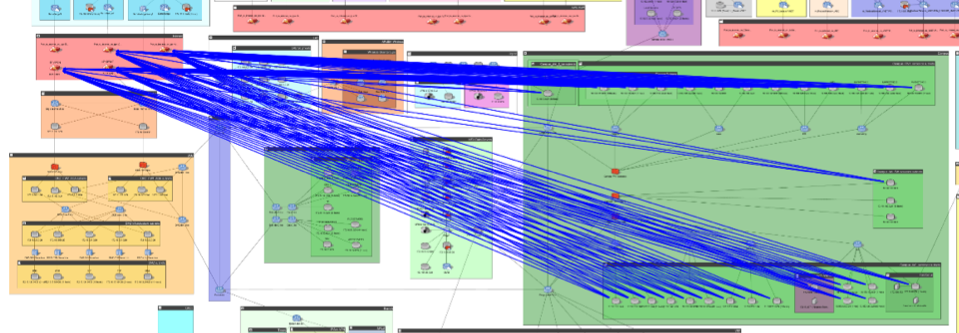
Figure 3: Access query results shown on map, showing existing access from internal assets to external THREAT COBRA infrastructure
With the results of the access query, the next step is to create additional controls such as firewall or routing rules to block access to the relevant IP address at your perimeter. To decide where to introduce such controls, you can run a RedSeal detailed path query to generate a visual traceroute of the offending access path(s) and identify which devices are along those paths and can be used to close access.
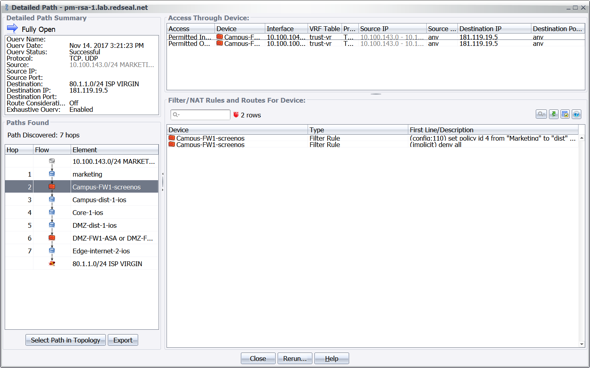
Figure 4: Detailed Path result identifying all network devices and relevant config locations mediating access from an internal asset to the HIDDEN COBRA infrastructure
2. Verify vulnerability scan coverage and perform a risk-based prioritization of vulnerabilities
The HIDDEN COBRA campaign has been known to use a set of five CVEs (CVE-2015-6585; CVE-2015-8651; CVE-2016-0034; CVE-2016-1019; CVE-2016-4117) as the vector for infection. These CVEs include several browser-based vulnerabilities for the Adobe Flash and Microsoft Silverlight plugins as well as a Korean word processing application. It is important to note that while these are the vulnerabilities known to be targeted in the wild to deliver Volgmer or FALLCHILL, any known or unknown Windows-based vulnerability that allows arbitrary code execution and/or privilege escalation can be used as part of a future spear phishing campaign. While it is crucial to locate and remediate the above CVEs first, it is important to perform a vulnerability scan of user workstations for all such vulnerabilities, not just the five enumerated ones.
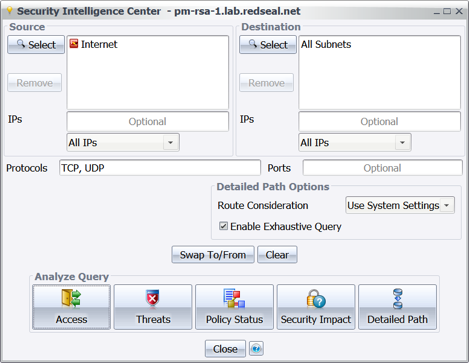
Figure 5: Using the Security Intelligence Center to execute a Threat Query to reveal which vulnerable assets are directly exploitable from the Internet
After importing the results of a vulnerability scan, vulnerability managers can first verify whether the scanner’s coverage was complete and identify any areas on the network missed by the scanner. This is accomplished by looking for all “Unscanned Subnets” model issues (MI-7) within your RedSeal model. A subsequent detailed path query from the scanner to the unscanned subnet will reveal whether and why access is blocked.
Next, you can perform a risk-based prioritization of the vulnerable hosts to ensure that the highest risk vulnerabilities are remediated first. The CVEs known to be actively exploited by the HIDDEN COBRA threat actors should be patched or otherwise mitigated first. A good start is to target the vulnerabilities that are on hosts that are accessible from untrusted networks, such as the Internet or a vendor’s network.
Since the malware attempts to establish a hidden Windows service with RAT capabilities, the next vulnerabilities to target for remediation are those that are directly or indirectly accessible and exploitable from any potentially compromised host. To find them, a RedSeal threat query can reveal all vulnerable hosts exploitable from a compromised endpoint on your network.
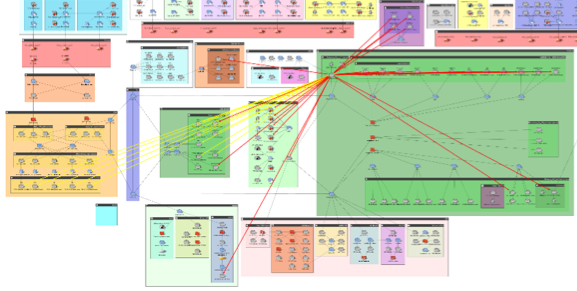
Figure 6: Visual results showing direct (red) and indirect (yellow) threats to the rest of the enterprise from a compromised host.
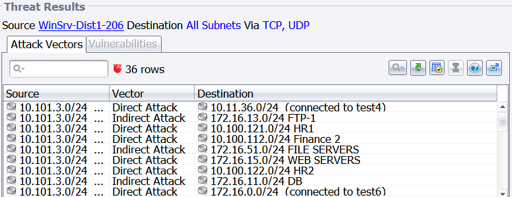
Figure 7: Threat Query results identifying vulnerable hosts threatened by the compromised endpoint
3. Investigate and contain existing IOCs
Finally, you can achieve greater resilience by accelerating your response to detected indicators of compromise and contain compromised systems while working to eliminate the infection. UC-CERT released several detection signatures to identify potentially compromised systems. By leveraging RedSeal’s incident response query directly or from our integrations with major SIEMs like QRadar, ArcSight, and Splunk, you can quickly assess the potential impact of a compromise and identify the mitigating controls necessary to isolate and contain it. The query allows incident responders to rapidly discover and prioritize by value all assets that are accessible from the vulnerable endpoint. A subsequent detailed path query between the vulnerable endpoint and a downstream critical asset will reveal all network devices mediating access and where controls such as firewall rules can be deployed to reduce downstream risk.
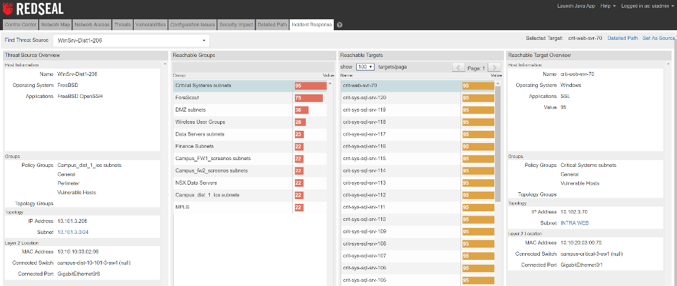
Figure 8: Incident Response query showing accessible groups and assets from the source of an indicator of compromise
Summary
The HIDDEN COBRA campaign is sophisticated, recently showing increases in intensity and variety of methods used. Defenders need to be resilient to minimize enterprise risk, efficiently mitigate damage, and recover from a successful compromise. RedSeal can help you achieve resilience in the face of these changing threats — by assessing ways to block outbound access to C2 nodes, by locating vulnerable and high risk internal machines, and by speeding the investigation of any detected indicators of compromise.
____________________
