Congratulations on StubHub Arrests
I would like to offer my congratulations to the private and public entities that participated in the recent investigation and arrests of cyber criminals in New York City, Ontario, Canada, and London, United Kingdom. A tremendous amount of hard work and dedication from all parties is required to successfully dismantle an international criminal enterprise. The success we witnessed this morning should be used as the gold standard upon which future collaboration between private companies and the International law enforcement community are modeled.

Continued success with prosecutions will have a lasting effect on cyber criminal behavior… but it is not a silver bullet. Cyber attacks and data breaches are still way too easy for attackers with even a moderate level of skill. We must continue working to make our systems and economy more resilient to attack.
I recently joined RedSeal Networks to work on this specific problem, making it easier for network owners to protect their assets and defend against intrusion and data breach. I’m looking forward to the coming months when we share more of our plan to make network security something that we aren’t just striving to attain, but something we actually have in our toolkit to counter cyber threats.

 This was brought home in a powerful way when I recently attended a cyber security meeting in London. In addition to briefings with a number of industry analysts, this meeting also included a panel discussion with about 15 CISOs from various industries like finance, not-for-profit, publishing, media, banking, and manufacturing. To a person these CISOs said two things. First, their greatest need was skilled personal to run their networks. Second, their senior management was asking questions about not “if” they were breached but what they would do “when” they were breached. This shift in attitude, driven by all the news in recent years about breaches at large, household-name companies, was an “ah ha” moment for me.
This was brought home in a powerful way when I recently attended a cyber security meeting in London. In addition to briefings with a number of industry analysts, this meeting also included a panel discussion with about 15 CISOs from various industries like finance, not-for-profit, publishing, media, banking, and manufacturing. To a person these CISOs said two things. First, their greatest need was skilled personal to run their networks. Second, their senior management was asking questions about not “if” they were breached but what they would do “when” they were breached. This shift in attitude, driven by all the news in recent years about breaches at large, household-name companies, was an “ah ha” moment for me. We’ve come a long way since then. So far, in fact, that the NSA has change their strategy in a way that should send a shiver down the back of everyone responsible for enterprise security: They have switched to assuming that security has been compromised.
We’ve come a long way since then. So far, in fact, that the NSA has change their strategy in a way that should send a shiver down the back of everyone responsible for enterprise security: They have switched to assuming that security has been compromised. on the equivalent of a guard sitting at one entrance expecting to see all access attempts when there are other doors to breach and a back fence that can be scaled.
on the equivalent of a guard sitting at one entrance expecting to see all access attempts when there are other doors to breach and a back fence that can be scaled. Today, governments across the world are applying their resources investing in full-time staff to break into systems and networks in other parts of the world. From the Syrian Electronic Army to the People’s Army, the US Government, and organized crime, attacks come from many different sources looking for a variety of results. This means the mentality is professional, organized, and coordinated, and the attackers are motivated by a variety of results, from financial to patriotic.the early days of people breaking into systems and networks, most actors were solo and focused on showing their own skills while demonstrating the weakness of those they attacked. Early viruses and worms (like the
Today, governments across the world are applying their resources investing in full-time staff to break into systems and networks in other parts of the world. From the Syrian Electronic Army to the People’s Army, the US Government, and organized crime, attacks come from many different sources looking for a variety of results. This means the mentality is professional, organized, and coordinated, and the attackers are motivated by a variety of results, from financial to patriotic.the early days of people breaking into systems and networks, most actors were solo and focused on showing their own skills while demonstrating the weakness of those they attacked. Early viruses and worms (like the 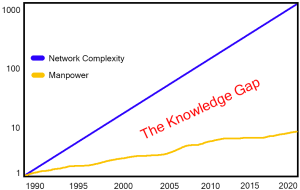 Have you found it easy to hire the talent you need? If so, lucky you – feel free to drop hints in the comments section (or just gloat – your peers tell me they aren’t having it so easy).
Have you found it easy to hire the talent you need? If so, lucky you – feel free to drop hints in the comments section (or just gloat – your peers tell me they aren’t having it so easy).