What Equifax Tells Us About Cybersecurity

By Richard A. Clarke
This month it is Equifax. Previously it was Yahoo and before that Target. Each new breach seems to set a new record of how many pieces of personal identifiable information have been compromised. It is easy to get inured to these news stories, especially since the media generally does not deduce any lessons from them. Many people come away thinking that data breaches are just something that we have to accept. But do we? What are we to take away from these recurring stories about huge hacks?
I have been working on cybersecurity for two decades now, initially from the White House and now in the private sector. Here is what I think should be our reaction to the Equifax story and similar breaches.
First, it is not impossible to secure major networks. Some companies and government agencies have quietly achieved sufficiently secure networks that they do not experience major data losses. It is, however, not easy to achieve.
Second, the essential ingredient to securing a network is not software or hardware. It is people – trained and skilled people. This country has an extreme shortage in such personnel. Despite the good salaries that are available in cybersecurity, there is a mismatch between what colleges are producing and what is needed. Colleges are simply under-producing cybersecurity graduates. There are hundreds of thousands of vacant jobs and even more positions that are being filled by under qualified staff.
Most colleges produce computer science majors or have graduate programs, however, they do not require education in cybersecurity as a condition for obtaining those degrees. Although it is sometimes derided by computer science faculty as too much like a “trade” and insufficiently academic, the truth is that cybersecurity is more difficult than basic computer science. Cybersecurity skills are built on top of knowledge about computer science.
In the absence of a focused and funded national initiative to significantly increase the number of cybersecurity trained graduates, corporations and government agencies will continue to fail at securing sensitive data.
Third, securing networks is expensive. Most companies spend only 3-5 percent of their Information Technology budget on security. These are the companies that get hacked. Most corporations have never properly priced in the cost of cybersecurity to their overall cost of doing business. There is a popular misconception in the business world about what it costs to run a major network. The original cost of security for a network was relatively low in the 1990s when most companies began building out their information technology infrastructure. The threat environment was significantly more benign then than it is now. Moreover, the security products available in the 1990s were limited to relatively inexpensive anti-virus, firewalls, and intrusion detection/prevention systems.
Today’s large networks require encryption, network discovery, threat hunting, data loss prevention, multifactor authentication, micro-segmentation, continuous monitoring, endpoint protection, intelligence reporting, and machine learning to detect and prioritize anomaly alarms. Corporations can no longer accurately be described in categories such as airlines, banks, or hospitals. They are all more accurately thought of as computer network companies that deal in aircraft, money management, or patients. If your company cannot do its business when your network goes down, then you are first and foremost an information technology company, one that specializes in whatever it is you do.
Fourth, because almost every American has now had their personally identifiable data stolen in one of these breaches, it should no longer be acceptable to use (or request) social security numbers, dates of birth, mother’s maiden names, and other publicly available identifiers to authenticate a user. Stop using them. Alliances of corporations should develop other, more advanced forms of identification that they would all use. In the jargon of the tech world, what we need are federated (more than one company employing it), multi-factor authentication. Even the government could use one or more of such systems, but if the government creates it there will be push-back from those fearing government abuse of civil liberties.
Finally, many companies and executives in them will continue to mismanage corporate cybersecurity and divulge sensitive data in the absence of significant penalties for failure. Today, even CEOs who are dismissed because of data breaches walk away with eye watering bonuses and severance packages. They do not suffer personally for their failure as managers.
Former White House cybersecurity official Rob Knake has observed that oil companies only got serious about oil spill prevention when they began to be fined based on the number of gallons that they spilled. He suggests that we hit companies that lose personally identifiable data with a heavy penalty for each bit of data compromised. In addition, companies should be required by federal law (not by the existing hodge-podge of conflicting state laws) to notify the government and individuals promptly when data has been compromised.
In sum, major cyber breaches do not have to be a regularly occurring phenomenon. They can be significantly reduced if we as a nation have a program to produce many more trained cybersecurity professionals, if corporations appropriately price in the cost of security, and if there are real financial consequences for companies that spill personal data into the hands of criminals and hostile nations.
Richard A. Clarke was Special Advisor to the President for Cybersecurity in the George W. Bush Administration and is the author of eight books including CYBER WAR.







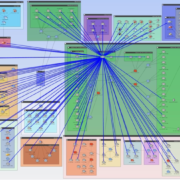
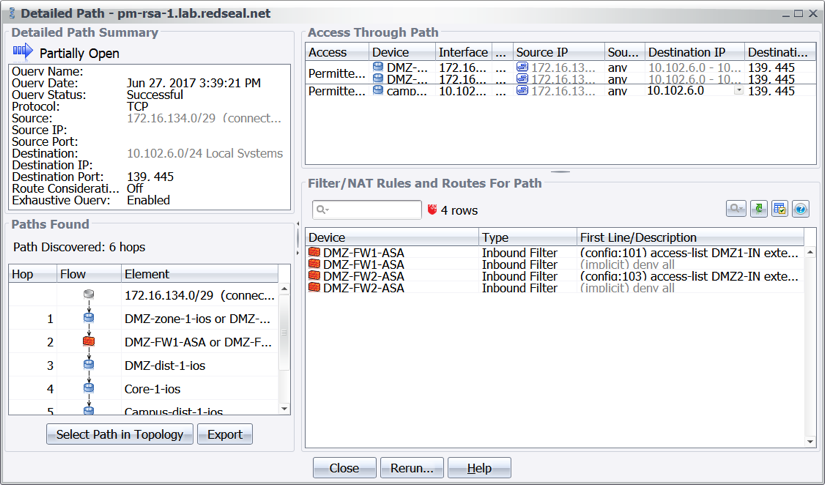
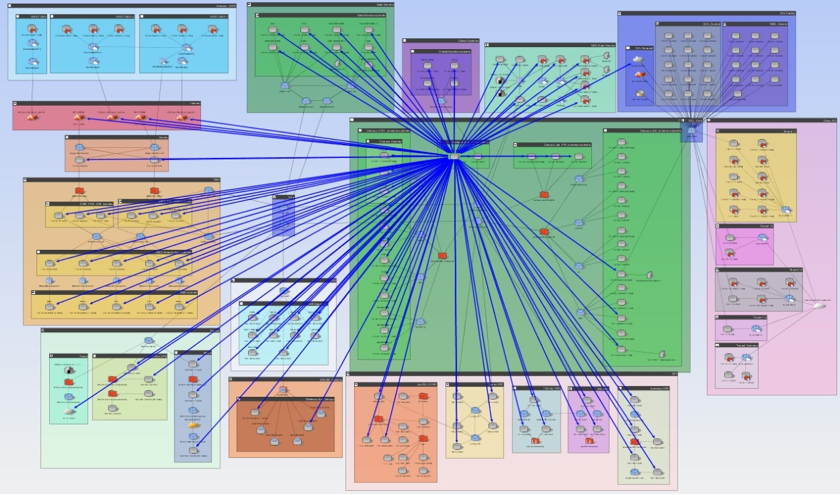 Figure 1: Visualizing all accessible areas of the network from a compromised system.
Figure 1: Visualizing all accessible areas of the network from a compromised system.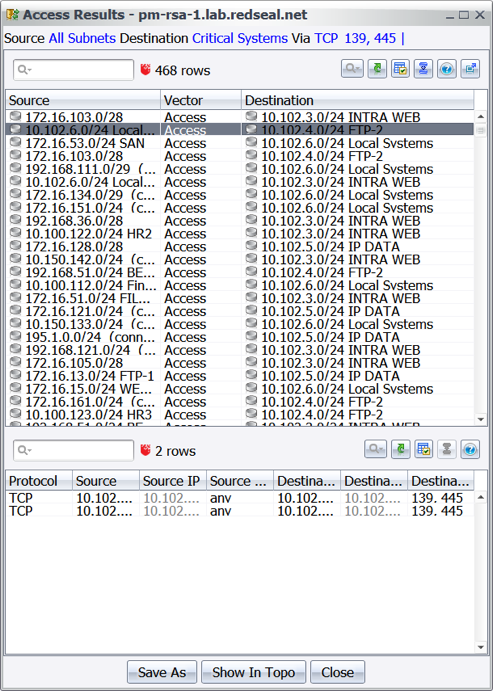 Figure 2 Results of an access query revealing what access exists from all subnets leading to the critical assets over TCP 139 or 445.
Figure 2 Results of an access query revealing what access exists from all subnets leading to the critical assets over TCP 139 or 445.