Digital Resilience Helps Mitigate or Prevent the ExPetr/NotPetya/ GoldenEye Malware
What is it?
The most recent malware campaign hitting Ukraine and the rest of the world is a wiper style malware which is packaged with several propagation mechanisms including the same weaponized Windows SMBv1 exploit utilized by WannaCry. What was initially thought to be a variant of the 2016 Petya ransomware has now been shown to be a professionally developed cyber-attack masquerading as run-of-the-mill ransomware gone wild. In fact, security researchers have demonstrated that, despite demanding a ransom payment, the payload irreversibly wipes the hard drives of infected systems with no way to decrypt even if a ransom is paid to the specified wallet.
Purpose & Impact
The motivation behind the attack appears to be one of destruction and disruption. Indeed, it has had a devastating impact on enterprise’s operations world-wide as it is designed to rapidly spread throughout corporate networks, irreversibly wiping hard drive in its wake. The initial infection is believed to have targeted Ukrainian businesses and government, managing to wreak havoc in the country’s financial, manufacturing, and transportation industries. Even Chernobyl radiation monitoring systems were impacted, forcing technicians to switch to manual monitoring of radiation levels. ExPetr managed to quickly spread worldwide to thousands of computers in dozens of countries with significant disruption to major enterprises across industries as varied as shipping, pharmaceuticals, and law. Over 50% of the companies being attacked worldwide are in the industrial manufacturing or oil & gas sectors.
How it Spreads
Researchers have identified several distinct mechanisms utilized by the ExPetr malware to penetrate enterprises’ perimeter defenses for an initial infection as well as lateral movement after a successful compromise. The malware’s lifecycle is split into three distinct phases: 1) initial infection, 2) lateral movement, and finally 3) wiping the compromised system. The initial infection is believed to have spread by a malicious payload delivered through a highjacked auto-update mechanism of accounting software used by businesses in Ukraine. Alternatively, ExPetr has been observed to achieve initial infection through phishing and watering hole attacks. Next, once inside, the malware utilizes a different array of techniques to self-propagate and move laterally. Critically, ExPetr attempts to infect all accessible systems with the same Windows SMBv1 vulnerability as last month’s WannaCry attack over TCP ports 445 and 139. The malware is also able to spread laterally by deploying credential stealing packages in search of valid admin and domain credentials. It will leverage any stolen credentials to copy itself through normal Windows file transfer functionality (over TCP ports 445 and 139) and then remotely execute the copied file using the standard administrative tools, PSEXEC or WMIC.
How Digital Resilience Helps
Because one of the primary ways the ExPetr malware spreads is through the same Windows SMBv1 vulnerability addressed by Microsoft’s MS17-010 patch in March 2017, the same prevention and mitigation techniques described in depth in RedSeal’s WannaCry response are effective. To review:
- Assess and limit exposure by using an access query to discover any assets accessible through TCP ports 445 or 139 from untrusted networks like the Internet or a 3rd party.
- Identify vulnerable hosts and prioritize remediation efforts based on risk to the enterprise by importing vulnerability scanner findings and sorting based on risk score.
- Isolate critical assets and contain high risk or compromised systems by discovering and eliminating unnecessary access to or from sensitive areas of the network.
- Continuously monitor compliance with network segmentation policies by analyzing the relevant rules in RedSeal’s Zones & Policy.
- Accelerate incident response by reactively or proactively discovering the blast radius from a compromised system, understanding which assets are network-accessible and deploying the relevant mitigating controls.
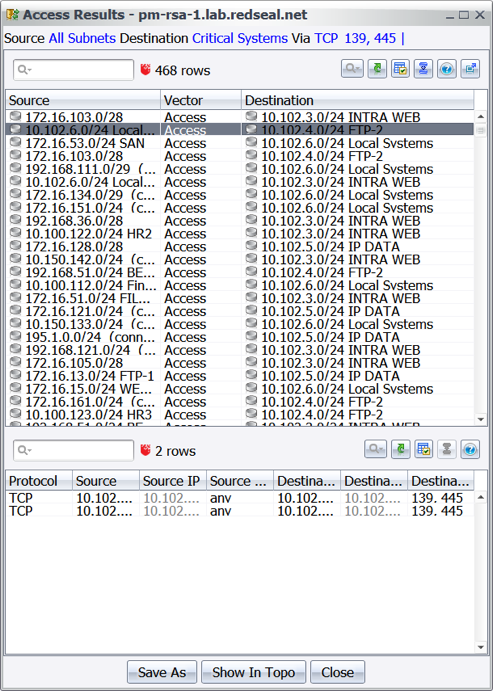
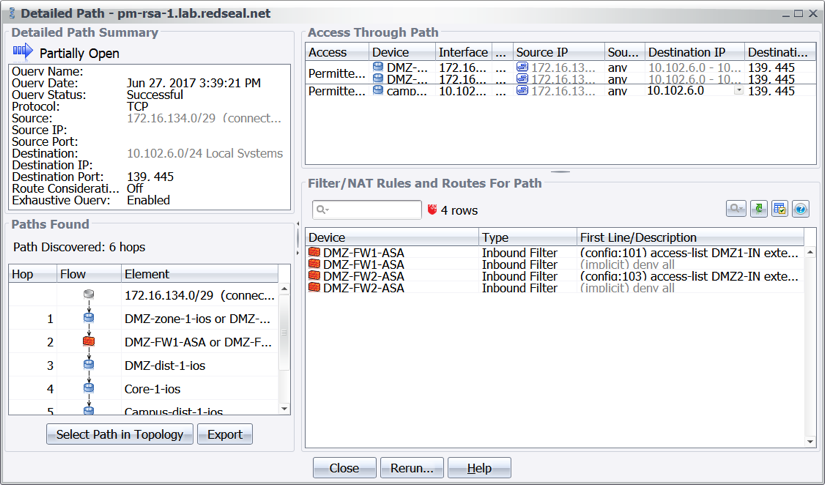
While applying the MS17-010 patch to vulnerable systems per a risk-based prioritization of vulnerable hosts is necessary, it is not sufficient to mitigate or prevent infection. ExPetr moves laterally through normal file-transfer and administrative capabilities using stolen credentials. As such, it is important to also reduce the attack surface of production and other mission critical assets through sensible network segmentation techniques, paying close attention to access over ports 445 and 139. RedSeal users can accomplish this by running an access query to determine what can reach critical systems through the implicated ports. Next, access that is not necessary or out of compliance can be cut off by examining the detailed path to see all network devices touched along the path and determine the optimal placement of a network countermeasure, such as a firewall rule, to eliminate the unnecessary access.
Figure 3 Detailed Path from the DMZ to a critical asset is 6 hops long with several routers and firewalls along the way
Conclusion
Cyber attacks are getting more efficient, more aggressive, and more destructive. Only a digitally resilient organization with full visibility into their network composition and security posture can hope to avoid falling victim, or to mitigate fallout in the event of compromise. Reducing your attack surface is essential to decreasing risk. This can best be done by adhering to standard IT best practices including implementing a robust backup strategy, a vulnerability management program, and a segmented internal network. In this day and age, network segmentation and micro-segmentation are increasingly important as attackers and malware routinely get past perimeter defenses, and often move laterally with impunity due to a lack of internal boundaries. RedSeal helps customers gain visibility into their network as it is built today, providing assurance through continuous monitoring of compliance with network access and segmentation policies. With the increased visibility and understanding, digitally resilient organizations can perform risk-based prioritization of remediation and mitigation activity to efficiently marshal resources and minimize overall enterprise risk.
For more information on how RedSeal can help you become resilient, please contact info@redseal.net.