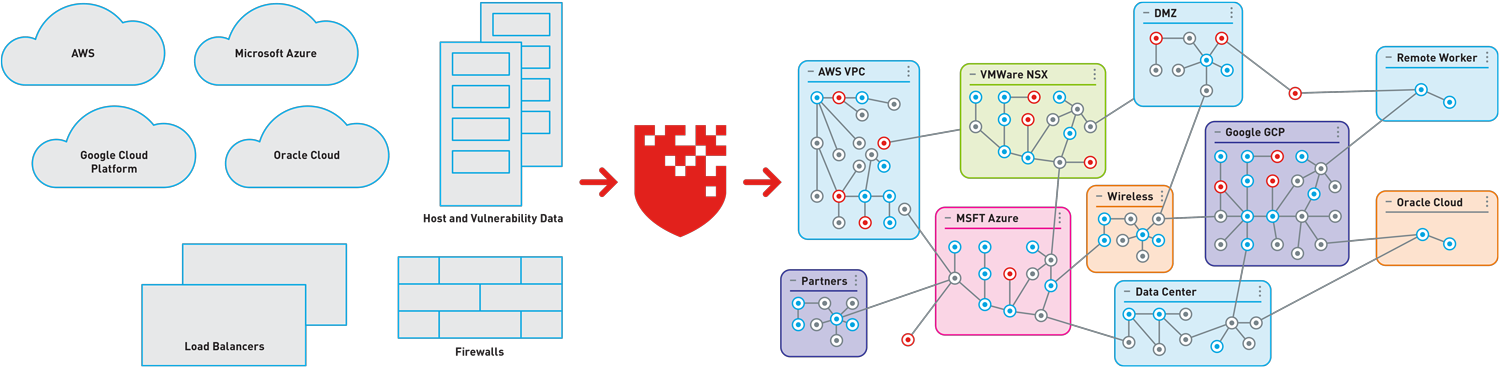
Modeling your hybrid network: the good, the bad, and the ugly
RedSeal ingests configuration information from your on-premises network devices including routers, switches, firewalls, and load balancers. It also accesses your public and private clouds via standard APIs and builds a connectivity model. RedSeal can also import host and vulnerability data from vulnerability scanners, endpoint protection tools, and other sources.
The complete connectivity model is done without agents, span ports, or taps and without being in line with production traffic or consuming NetFlow data.
With this information, RedSeal uses its patented algorithms to calculate an accurate model of your hybrid network. It calculates how data can move through it plus the net effective reachability to the resources and/or any lateral movement. You can liken this to the roads on a map. RedSeal can show you how (or if) data can move from any point to another.
Next, RedSeal overlays the instance, host, and endpoint information, along with identified vulnerabilities. This is like placing houses and buildings along the roads—with information about broken doors and windows.
But, RedSeal goes above and beyond mapping. It delivers a model: a visual, responsive model you can update daily, ask questions, and learn from.