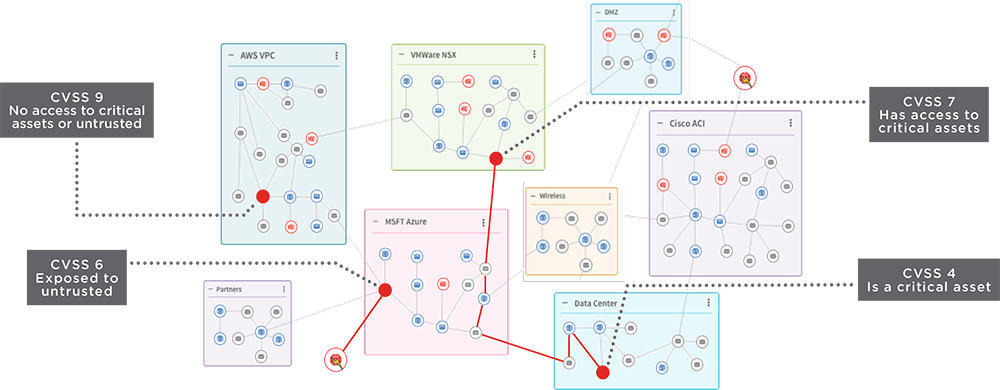
Prioritize vulnerabilities with most impact
RedSeal’s cyber terrain analytics platform can improve your network vulnerability security management program at each step of the process.
By adding network context into your enterprise network vulnerability management program, RedSeal enables you to perform a true risk-based vulnerability prioritization of the findings from your existing scanners. And, by comparing your scan data with a continuously updated RedSeal model of your network, RedSeal helps identify which assets to target for scanning, and helps identify and resolve any gaps in your network vulnerability scanner coverage. RedSeal’s cyber network vulnerability assessment calculates vulnerability risk scores that take into account not only vulnerability severity and asset value, but also downstream risk based on the accessibility of vulnerable downstream assets. As a result, network vulnerability managers are able to identify and target the vulnerabilities that are creating the most risk in your unique network environment.
With RedSeal as part of your enterprise network vulnerability security management program, you’ll be able to:
- Identify assets that have not been scanned by a vulnerability management tracking tool.
- Identify the network devices and specific access rules preventing scanner access.
- Prioritize network vulnerabilities for remediation or mitigation based on risk — risk-based vulnerability is calculated in the context of your network, business, and vulnerability management best practices.
- Visualize all reachable assets for optimal scanner placement.
- Efficiently triage and plan mitigation of unpatchable vulnerabilities through containment or isolation.
RedSeal’s platform adds value to each phase of a network vulnerability management program: discovery, assessment, triage, and vulnerability remediation and mitigation.
- Discover assets: Generate scanner target lists and identify assets that have not been scanned.
- Perform cyber vulnerability risk assessment: Identify network devices and configuration rules preventing scanner access. Visualize all reachable assets for optimal scanner placement.
- Triage findings: Perform risk-based vulnerability prioritization based on your network context, taking into account severity, asset value, as well as upstream and downstream access.
- Remediate and mitigate vulnerability issues: Identify precise access paths and devices to update in order to isolate and contain vulnerable assets that can’t be patched.