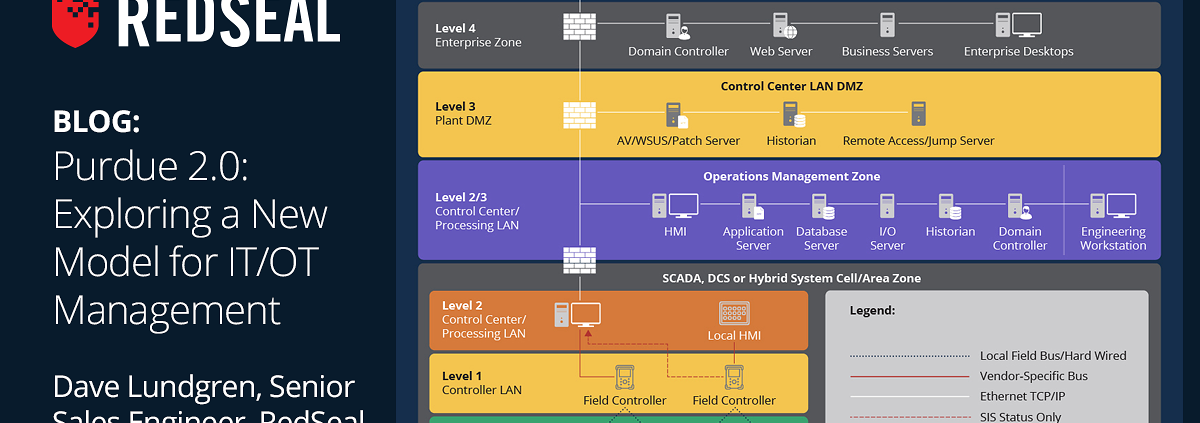
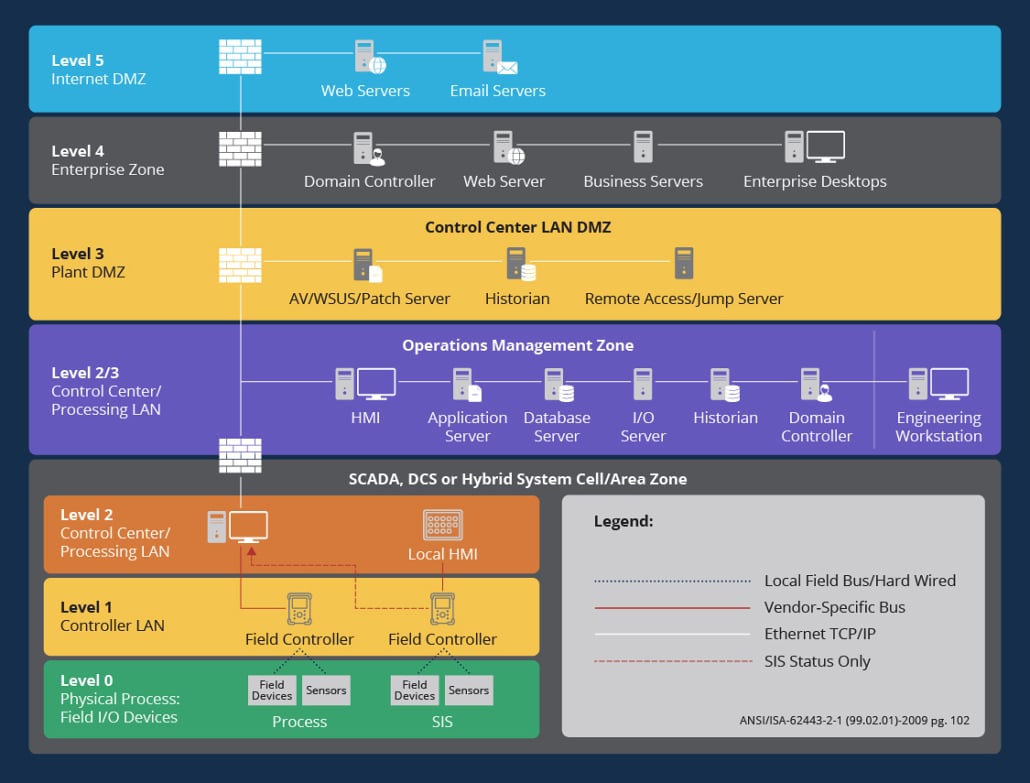
Why Visualizing the Entire Healthcare Attack Surface Is Critical
In recent years, the healthcare sector has been steadily adopting web and cloud-based technologies and shifting towards an internet-enabled system to improve quality of care.
However, along with the limitless benefits that the internet offers — like sharing information, simplifying operational processes, tracking workflows, enhancing connectivity, and storing and organizing data — is an increased risk of cyberattacks, data breaches, and other types of fraud. This makes hospitals and healthcare organizations increasingly vulnerable to advanced threats and targeted attacks.
According to recent reports, data breaches in the healthcare sector have been rising at an alarming rate for the last five years. In 2020, during the COVID-19 pandemic, email-based attacks increased by 42%, so it’s no wonder that more and more healthcare organizations are adopting a robust, multi-faceted strategy to improve their security posture. Hospitals’ expanding digital footprint also complicates their network infrastructures, making complete visibility into the entire attack surface extremely essential to managing cyber risks effectively.
Expanding Healthcare Attack Surface Risks
The widespread use of wireless technology is undoubtedly beneficial to the healthcare system. Wireless technology enables healthcare IT infrastructures to run data center servers, medical equipment, tools and applications, and other devices like smartphones, tablets, and USB drives. Organizations stay connected to deliver effective operations and consistently informed care.
These connected devices help in patient monitoring, medication management, workflow administration, and other healthcare needs. However, the increased number of devices connecting to the network also broadens the attack surface — meaning more entry points for unauthorized access and therefore the need for enhanced infrastructure visibility to mitigate risks.
Why Complete Visualization Is Essential
From booking an appointment to setting foot in the doctor’s clinic or hospital, patients go through several processes and interact with different interconnected devices and software systems. While a connected environment ensures a seamless patient experience, the different touch points provide more opportunities for attackers to gain access to sensitive data.
Currently, there are 430 million linked medical devices deployed globally, connected through Wi-Fi, Bluetooth, and radio transmission. The sheer amount of sensitive and personal information healthcare systems capture and process is why their systems are desirable targets. Therefore, it is critical to safeguard the data stored in these systems.
Protected health information (PHI), such as credit card and bank account numbers, and personal identification information (PII), such as social security numbers, are data cybercriminals find particularly alluring. Selling this sensitive information on the dark web is a very profitable business.
Even just a small part of the healthcare technology spectrum may lead to the greatest cybersecurity gaps, allowing criminals to exploit vulnerabilities and gain access to sensitive data. The resulting cyber crimes directly impact organizational productivity and brand reputation.
Here are a few risks that are most detrimental to healthcare businesses’ bottom lines and reputations.
- Ransomware: Healthcare services are notably vulnerable to ransomware attacks because they depend on technology to a significant extent, considering the nature of their day-to-day operations. Health records are highly rewarding for criminals because each patient, hospital, or confidential record can command a hefty price in the underground market.
- Phishing: Phishing attacks are quite common in healthcare. Attackers target the most vulnerable link in the security chain, i.e., people, to make their jobs easier. Through social engineering, users click on malicious attachments or links, thereby infecting their systems and losing access. The repercussions can be disastrous and the losses unimaginable. For instance, a Georgia diagnostics laboratory recently discovered that an employee’s compromised email account led to a phishing attack, impacting 244,850 individuals. The attackers were able to acquire patient information and then attempted to divert invoice payments.
- Cloud Storage Threats: Many healthcare providers are now switching to cloud-based storage solutions for better connectivity and convenience. Unfortunately, not every cloud-based solution is HIPAA-compliant, making them clear targets for intruders. Healthcare companies must implement access restrictions more carefully and encrypt data properly before transmitting. Additionally, complete visualization of the attack surface is necessary to prevent data breaches, data leaks, improper access management, and cloud storage misconfiguration.
How to Protect Expanding Healthcare Attack Surfaces
Attack surface analysis can help identify high-risk areas, offering an in-depth view of the entire system. This way, you can better recognize the parts that are more vulnerable to cyber threats and then review, test, and modify the security strategies in place as necessary.
Healthcare IT administrators must secure the network infrastructure using stringent policies and procedures like enforcing strong passwords, properly configuring firewalls, setting up user access permissions, and ensuring authorized access to assets and resources. They must also monitor and properly configure all the devices connected to the network — be it standard healthcare devices or personal devices of patients and workers. In addition, a strong encryption policy can help increase data security, making it difficult for cyber attackers to penetrate the system.
Conducting regular attack surface scans can also mitigate cyberattack risks. This helps ensure security control measures are adequate and that decision-makers have the data they need to make informed decisions regarding the organization’s cybersecurity strategy. Also, all types of software and related updates for medical devices must be tested prior to installation.
Secure Your Entire Healthcare Network with RedSeal
Healthcare organizations often hesitate to invest in cloud security solutions. But the average cost of a healthcare breach is $9.23 million, which is far more than the cost of professional cloud security solutions. Additionally, healthcare institutions deal with extremely sensitive information, and fines for data security noncompliance can be extremely costly. Healthcare security leaders must be able to effectively visualize their entire attack surface to bolster their cybersecurity defenses.
RedSeal offers award-winning cloud security solutions that provide comprehensive, dynamic visualization of all connected devices. We partner with leading network infrastructure suppliers to provide comprehensive network solutions and professional services. This way, you can see and secure your entire network environment.
Contact us to learn how we can help strengthen your network security.