Are Your Corporate Assets and Remote Workforce Protected as You Deploy Cisco Meraki Devices?
Cisco’s Meraki products provide a seamless connection for your remote workforce, but are you confident that they are securely connected?
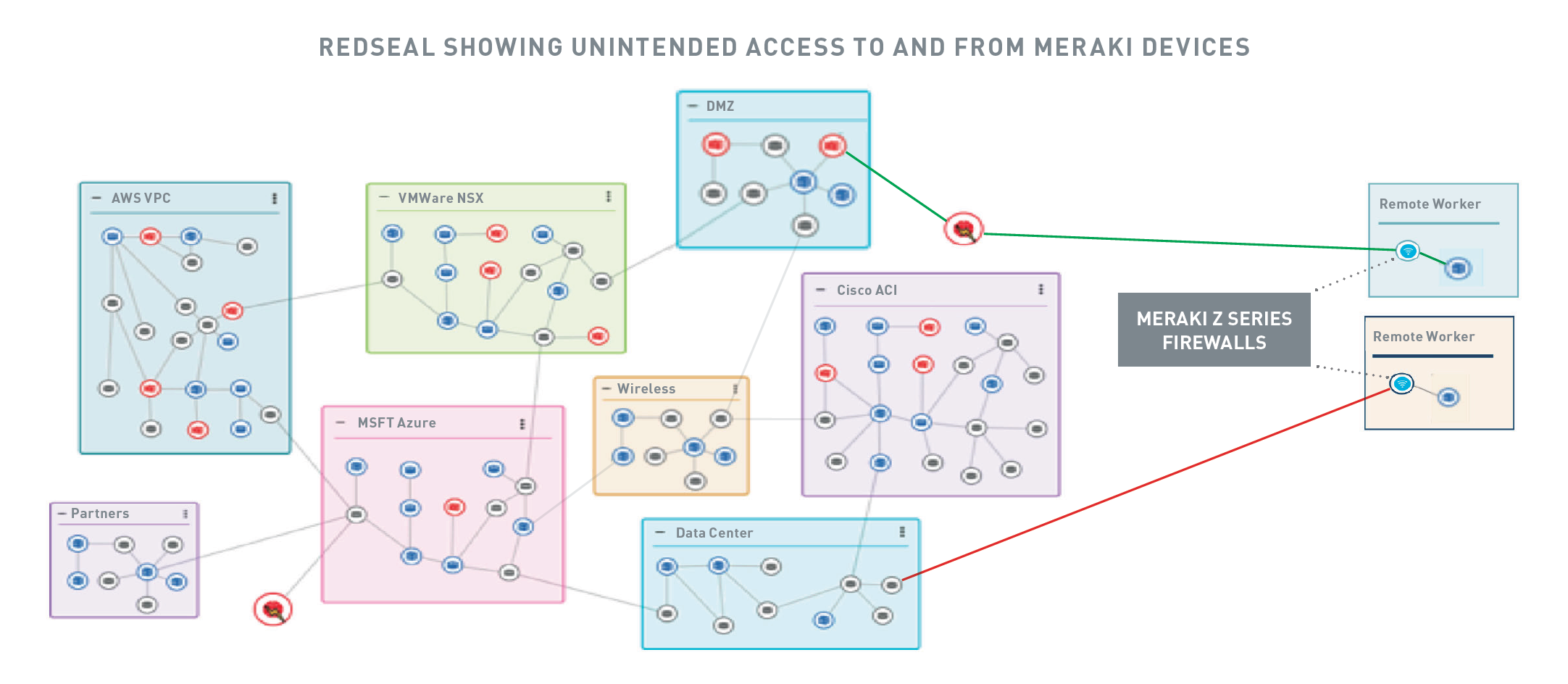
A misconfiguration can unintentionally expose your corporate assets to unauthorized users – or provide an unmonitored path for data exfiltration. Validating all Meraki devices across your network can be a formidable challenge. Visibility into Meraki devices and their connections wherever they are, offers both validation and peace of mind.
RedSeal’s experienced team of cybersecurity consultants can give you the intelligence you need by showing you what’s on your network and how it’s connected and what’s at risk. RedSeal gives you visibility across hybrid cloud and on-premise environments — from Meraki devices to your data centers. Our security professionals can provide all the necessary insights and explain the associated risks so that you can make an informed decision.