Data, Data Everywhere, nor Any Time to Think
I remember when I first started trying to solve network security problems, using fancy network analytics. I applied the classic suspension of disbelief that’s necessary to work on any emerging technology – first, you assume all the hard problems will be easy, and second, you assume the impossible ones will just go away. Happily, much of this is true – it’s funny how well it works. Only later do you learn which problems are the truly hard ones.
What’s hard about network security analytics? Well, not the security, and not the analytics – we’ve found we can do plenty on both of those that pays off really well, given the data. The pesky data, now that’s a different kettle of enchiladas.
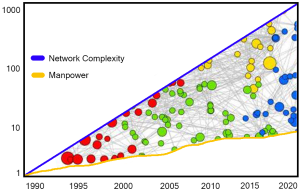
But then what? Typical security organizations are drowning in data, so how can I complain about needing more? Well, facts are just facts; useful information, or better yet, actionable intelligence is something else altogether. We stockpile data from sensors, but we struggle to find useful signal in there. We deploy automated signal reduction engines, but they just turn mountains of alerts into hills of alerts, and we still don’t have time or people enough to climb those. And along come these network security analytics people saying “what you need is more data”. Hmmm.
Of course, what we need is the RIGHT data, processed the right way, at the right time.

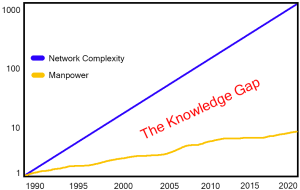 Have you found it easy to hire the talent you need? If so, lucky you – feel free to drop hints in the comments section (or just gloat – your peers tell me they aren’t having it so easy).
Have you found it easy to hire the talent you need? If so, lucky you – feel free to drop hints in the comments section (or just gloat – your peers tell me they aren’t having it so easy).