Accelerate Incident Response and Investigations

Knowing which hosts are involved in a security incident is critical information for anyone who is an incident handler. The quicker the attackers and their targets can be identified the quicker the incident can be stopped. Collecting this information from a plethora of systems and log sources can be difficult and time consuming. Compounding the problem even further Forrester reported that “62% of enterprise security decision makers report not having enough security staff[1].” Lack of resources and time spent verifying devices instead of dealing with the threat right away contribute to the damage done by threat actors.
For an incident response team to perform their job effectively, on top of understanding and responding to threats, they need to understand the network. This includes all entrances to a network, the route information flows through their network, the critical systems needed to run their business, the location of the critical systems within their network, and an understanding of how the attack can spread once the network is compromised. Understanding the network and the topology is the foundation of any good incident response team. How do you protect and contain an outbreak if you don’t understand how it spreads? The network is the medium in which it spreads.
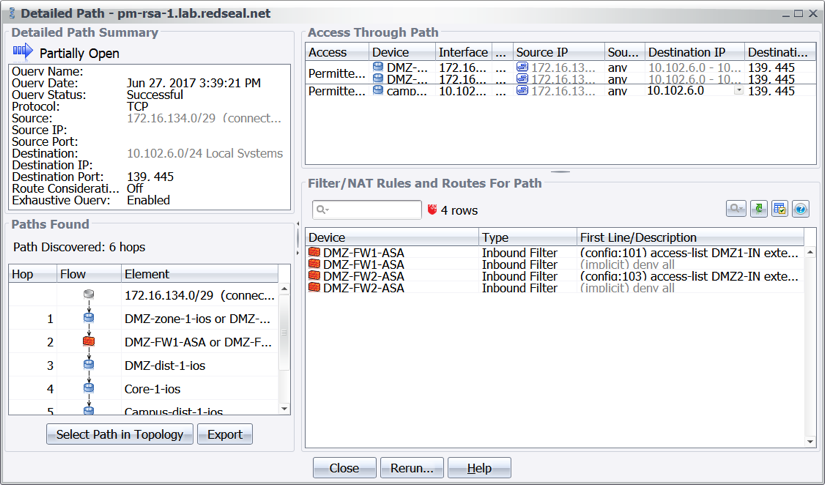
Allowing your incident response team to access the RedSeal appliance will drop your “average time to achieve incident resolution” and “time to containment” KPIs. RedSeal ingests all network device configurations and will show the paths information takes, where the attacks are coming from, and where the targets exist within your network. RedSeal simplifies locating devices by parsing through the NAT, VPN, and Load Balancer configuration files with only a few clicks of the mouse. In a matter of minutes, the incident response team will be able to find where both the target and the attacker exist on the network as well as the path the attack traffic is taking. Otherwise, in most situations, incident response must parse through and follow routing tables manually or engage the network team to get an understanding of the path.
Another challenge incident response teams face is overlooking subnets and devices, especially in large and complex organizations. RedSeal will shine light onto forgotten devices and subnets. Again, with a few clicks of a mouse, RedSeal will analyze the configurations and report if there is a direct connection from untrusted zones to these devices. Once found, the devices can be hardened against threats and appropriate decisions can be made to take them offline, upgrade, or migrate them to a more protected area of the network.
An incident response team’s main goal is to keep the level of impact to an organization down to an acceptable level. It is the time between detection and containment that has the biggest impact on mitigating the severity of the incident and data loss. Stopping the threat faster, before it spreads, also means fewer resources spent in recovering from the impact of the incident. RedSeal reduces the amount of time incident response spends identifying targets, moves the team to stopping the incident faster, and improves your organization’s resiliency against attacks.
[1] Forrester “Breakout Vendors: Security Automation and Orchestration.”
To learn more about how RedSeal can accelerate your incident response, watch our animated video, or contact us.

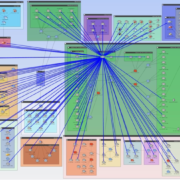
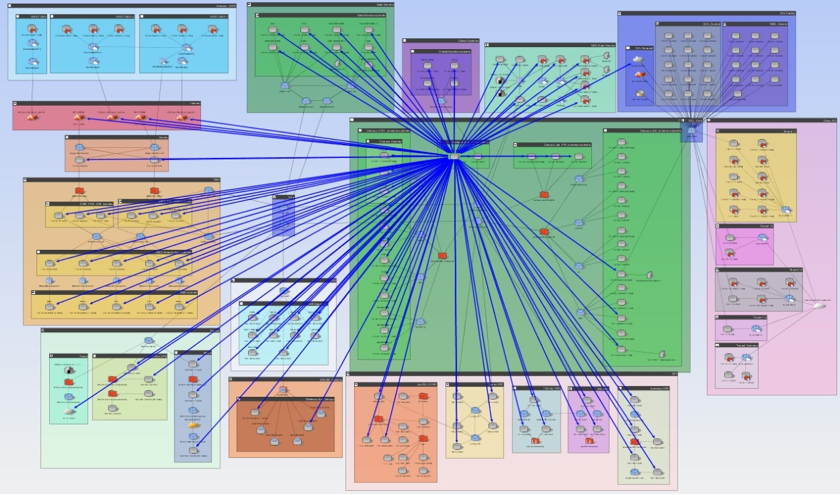 Figure 1: Visualizing all accessible areas of the network from a compromised system.
Figure 1: Visualizing all accessible areas of the network from a compromised system.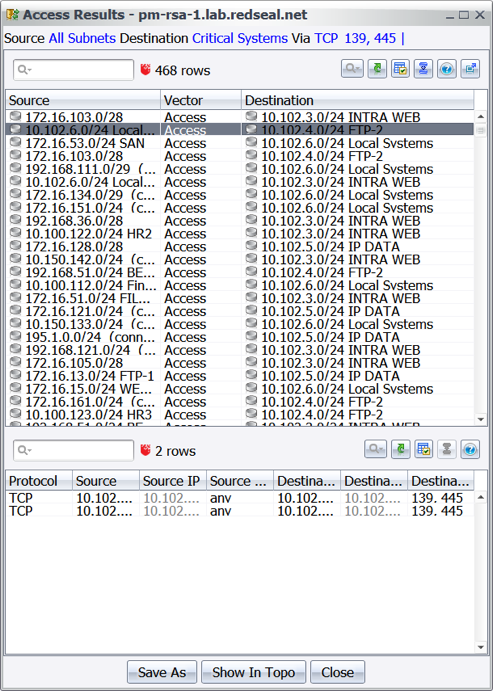 Figure 2 Results of an access query revealing what access exists from all subnets leading to the critical assets over TCP 139 or 445.
Figure 2 Results of an access query revealing what access exists from all subnets leading to the critical assets over TCP 139 or 445.